Cybersecurity Trends 2025: Navigating the Evolving Threat Landscape
Related Articles: Cybersecurity Trends 2025: Navigating the Evolving Threat Landscape
Introduction
In this auspicious occasion, we are delighted to delve into the intriguing topic related to Cybersecurity Trends 2025: Navigating the Evolving Threat Landscape. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Cybersecurity Trends 2025: Navigating the Evolving Threat Landscape
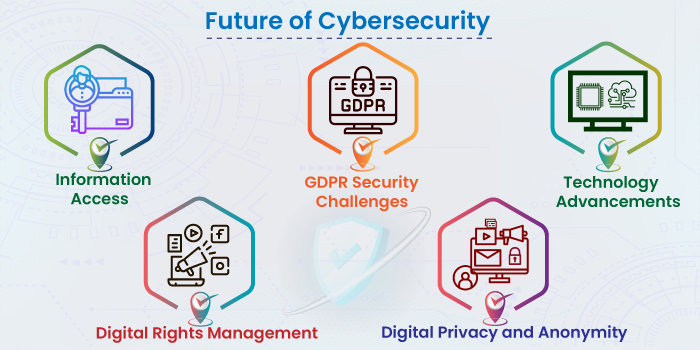
The digital landscape is constantly evolving, and with it, the methods and motives of cybercriminals. As technology advances, so too do the threats it faces. To effectively combat these evolving threats, organizations and individuals must anticipate and adapt to cybersecurity trends 2025.
This comprehensive analysis explores the key trends shaping the cybersecurity landscape in 2025, examining the evolving threats, emerging technologies, and the crucial role of proactive strategies.
The Shifting Threat Landscape
The threat landscape is becoming increasingly sophisticated and complex. Cybercriminals are constantly innovating, leveraging new technologies and exploiting vulnerabilities to achieve their objectives.
1. The Rise of AI-Powered Attacks
Artificial intelligence (AI) is transforming various industries, and cybersecurity is no exception. While AI can be a powerful tool for defending against threats, it is also being weaponized by attackers.
- AI-driven phishing attacks: AI can generate highly personalized and convincing phishing emails, making it harder for users to discern legitimate communications from malicious ones.
- Automated malware development: AI can expedite the creation of new malware variants, enabling attackers to launch more targeted and sophisticated attacks.
- AI-powered reconnaissance: AI can be used to gather information about potential targets and identify vulnerabilities, allowing attackers to plan more effective attacks.
2. The Growing Importance of IoT Security
The Internet of Things (IoT) is rapidly expanding, connecting billions of devices to the internet. This interconnectedness brings numerous benefits but also creates significant security vulnerabilities.
- Increased attack surface: The proliferation of IoT devices expands the attack surface, offering more entry points for attackers.
- Data security concerns: IoT devices often collect sensitive personal data, making them prime targets for data breaches.
- Lack of security standards: Many IoT devices lack robust security features, making them easy targets for exploitation.
3. The Evolution of Ransomware Attacks
Ransomware attacks have become increasingly prevalent and sophisticated. Attackers are now targeting critical infrastructure and demanding higher ransoms, causing significant disruption and financial losses.
- Double extortion: Attackers are increasingly resorting to double extortion, where they not only encrypt data but also threaten to leak it publicly if the ransom is not paid.
- Ransomware-as-a-service (RaaS): The emergence of RaaS platforms has made it easier for individuals with limited technical skills to launch ransomware attacks.
- Targeting of critical infrastructure: Attackers are increasingly targeting critical infrastructure, such as power grids and hospitals, to cause maximum disruption and impact.
4. The Growing Threat of Supply Chain Attacks
Supply chain attacks target vulnerabilities in an organization’s supply chain, compromising its systems and data. These attacks are often difficult to detect and can have devastating consequences.
- Software supply chain attacks: Attackers target software development processes, introducing malicious code into software that is then distributed to users.
- Hardware supply chain attacks: Attackers compromise hardware components during the manufacturing process, introducing backdoors or other vulnerabilities.
- Third-party vendor attacks: Attackers exploit vulnerabilities in third-party vendors, gaining access to an organization’s systems and data.
5. The Rise of Cybercrime-as-a-Service (CaaS)
CaaS platforms provide individuals with limited technical skills access to tools and resources for launching cyberattacks. This makes it easier for attackers to carry out sophisticated attacks without significant technical expertise.
- Malware-as-a-service (MaaS): Platforms that offer ready-made malware for use in attacks.
- Botnet-as-a-service (BaaS): Platforms that provide access to botnets, networks of compromised computers that can be used to launch distributed denial-of-service (DDoS) attacks and other malicious activities.
- Phishing-as-a-service (PaaS): Platforms that provide tools for creating and launching phishing campaigns.
Emerging Technologies and Their Impact on Cybersecurity
The emergence of new technologies presents both opportunities and challenges for cybersecurity. While these technologies can enhance security capabilities, they also introduce new vulnerabilities that attackers can exploit.
1. The Role of Blockchain in Cybersecurity
Blockchain technology offers several potential benefits for cybersecurity, including:
- Enhanced data security: Blockchain’s decentralized and immutable nature makes it difficult for attackers to tamper with data.
- Improved trust and transparency: Blockchain can be used to track the provenance of data and ensure its authenticity.
- Secure identity management: Blockchain can be used to create secure digital identities, reducing the risk of identity theft.
2. The Impact of Cloud Computing on Cybersecurity
Cloud computing offers numerous benefits, but it also presents new security challenges:
- Shared responsibility model: Cloud providers are responsible for securing their infrastructure, but organizations are responsible for securing their data and applications in the cloud.
- Data security concerns: Organizations must ensure that their data is securely stored and protected in the cloud.
- Compliance requirements: Organizations must comply with various regulations and standards when storing and processing data in the cloud.
3. The Rise of Zero Trust Security
Zero trust security is a security framework that assumes no user or device can be trusted by default. It requires organizations to verify every request and enforce least privilege access controls.
- Stronger authentication: Zero trust security relies on multi-factor authentication and other strong authentication mechanisms to verify user identities.
- Fine-grained access control: Access to resources is granted based on user identity, device context, and other factors, ensuring that only authorized users have access to the data and applications they need.
- Continuous monitoring and threat detection: Zero trust security includes continuous monitoring and threat detection capabilities to identify and respond to suspicious activity.
4. The Potential of Quantum Computing for Cybersecurity
Quantum computing has the potential to revolutionize cybersecurity, but it also poses significant threats:
- Enhanced cryptography: Quantum computing can be used to break current encryption algorithms, making data more vulnerable to attack.
- New attack vectors: Quantum computers can be used to develop new attack vectors that are not possible with traditional computers.
- Post-quantum cryptography: Researchers are working on developing new cryptographic algorithms that are resistant to quantum attacks.
Proactive Cybersecurity Strategies for 2025
Organizations must adopt a proactive approach to cybersecurity to mitigate the risks posed by evolving threats.
1. Implementing a Comprehensive Security Strategy
A comprehensive security strategy should encompass all aspects of an organization’s IT infrastructure, including:
- Risk assessment: Identifying and prioritizing security risks.
- Vulnerability management: Identifying and patching vulnerabilities in systems and applications.
- Security awareness training: Educating employees about security best practices and common threats.
- Incident response planning: Developing a plan for responding to security incidents.
2. Investing in Cybersecurity Technologies
Organizations must invest in the latest cybersecurity technologies to stay ahead of evolving threats.
- Next-generation firewalls: Firewalls that use advanced threat detection techniques to block malicious traffic.
- Intrusion detection and prevention systems (IDS/IPS): Systems that detect and prevent malicious activity on networks.
- Endpoint security solutions: Software that protects endpoints from malware and other threats.
- Data loss prevention (DLP) solutions: Software that prevents sensitive data from leaving the organization’s network.
3. Embracing a Culture of Security
Organizations must foster a culture of security, where security is everyone’s responsibility.
- Security awareness training: Educating employees about security best practices and common threats.
- Security policies and procedures: Implementing clear security policies and procedures that employees are expected to follow.
- Reporting security incidents: Encouraging employees to report suspicious activity.
4. Building Partnerships with Cybersecurity Experts
Organizations can benefit from partnering with cybersecurity experts to strengthen their security posture.
- Managed security services providers (MSSPs): Outsourcing security functions to specialized providers.
- Security consulting firms: Engaging with security experts to provide guidance and support.
- Cybersecurity research organizations: Collaborating with research organizations to stay informed about emerging threats.
Related Searches
1. Cybersecurity Trends in 2025: This search term focuses on understanding the key trends shaping the cybersecurity landscape in the coming years.
2. Future of Cybersecurity: This search term explores the long-term outlook for cybersecurity, considering emerging technologies and evolving threats.
3. Top Cybersecurity Threats in 2025: This search term focuses on identifying the most significant threats facing organizations in 2025.
4. Cybersecurity Best Practices: This search term seeks information on effective security practices that organizations can implement to mitigate risks.
5. Cybersecurity for Small Businesses: This search term targets small businesses seeking to understand the specific cybersecurity challenges they face and how to address them.
6. Cybersecurity Awareness Training: This search term focuses on finding resources for cybersecurity awareness training programs for employees.
7. Cybersecurity Jobs: This search term explores the growing demand for cybersecurity professionals and the skills required for these roles.
8. Cybersecurity Regulations: This search term seeks information on relevant cybersecurity regulations and compliance requirements.
FAQs by Cybersecurity Trends 2025
1. What are the biggest cybersecurity challenges facing organizations in 2025?
The biggest cybersecurity challenges in 2025 will likely include AI-powered attacks, the growing number of connected devices, the evolution of ransomware, and the increasing sophistication of supply chain attacks.
2. How can organizations prepare for the rise of AI-powered attacks?
Organizations can prepare for AI-powered attacks by implementing robust security controls, investing in AI-driven security solutions, and providing employees with cybersecurity awareness training.
3. What are the key considerations for securing IoT devices?
Securing IoT devices requires careful consideration of device security features, data encryption, access control, and regular updates.
4. How can organizations mitigate the risks of ransomware attacks?
Organizations can mitigate ransomware risks by implementing strong data backups, regularly updating software, and educating employees about ransomware threats.
5. What steps can organizations take to protect themselves from supply chain attacks?
Organizations can protect themselves from supply chain attacks by carefully vetting vendors, implementing secure software development practices, and monitoring their supply chains for vulnerabilities.
6. How can organizations adopt a zero trust security model?
Adopting a zero trust security model involves implementing strong authentication, fine-grained access control, and continuous monitoring and threat detection.
7. What are the implications of quantum computing for cybersecurity?
Quantum computing poses both opportunities and threats for cybersecurity. It has the potential to break current encryption algorithms, but it also offers the possibility of developing new, more secure algorithms.
8. How can organizations create a culture of security?
Creating a culture of security requires educating employees about security best practices, implementing clear security policies and procedures, and encouraging employees to report suspicious activity.
Tips by Cybersecurity Trends 2025
1. Stay informed about emerging threats: Subscribe to cybersecurity news sources, attend industry events, and engage with cybersecurity experts to stay informed about the latest threats.
2. Implement a proactive security strategy: Don’t wait for a breach to occur. Implement a comprehensive security strategy that addresses all aspects of your organization’s IT infrastructure.
3. Invest in cybersecurity technologies: Don’t skimp on security investments. Invest in the latest cybersecurity technologies to stay ahead of evolving threats.
4. Train employees on security best practices: Employees are often the weakest link in an organization’s security chain. Provide them with regular cybersecurity awareness training.
5. Partner with cybersecurity experts: Don’t go it alone. Partner with cybersecurity experts to strengthen your security posture.
6. Regularly review and update your security controls: The threat landscape is constantly evolving. Regularly review and update your security controls to ensure they remain effective.
7. Prepare for security incidents: Develop a comprehensive incident response plan that outlines how your organization will respond to security incidents.
8. Embrace a culture of security: Create a culture where security is everyone’s responsibility.
Conclusion
Cybersecurity trends 2025 are shaping a future where organizations must be more proactive and adaptable than ever before. The rise of AI-powered attacks, the proliferation of IoT devices, and the evolution of ransomware are just a few of the challenges organizations will face. However, by embracing emerging technologies, implementing comprehensive security strategies, and fostering a culture of security, organizations can mitigate the risks and navigate the evolving threat landscape successfully.


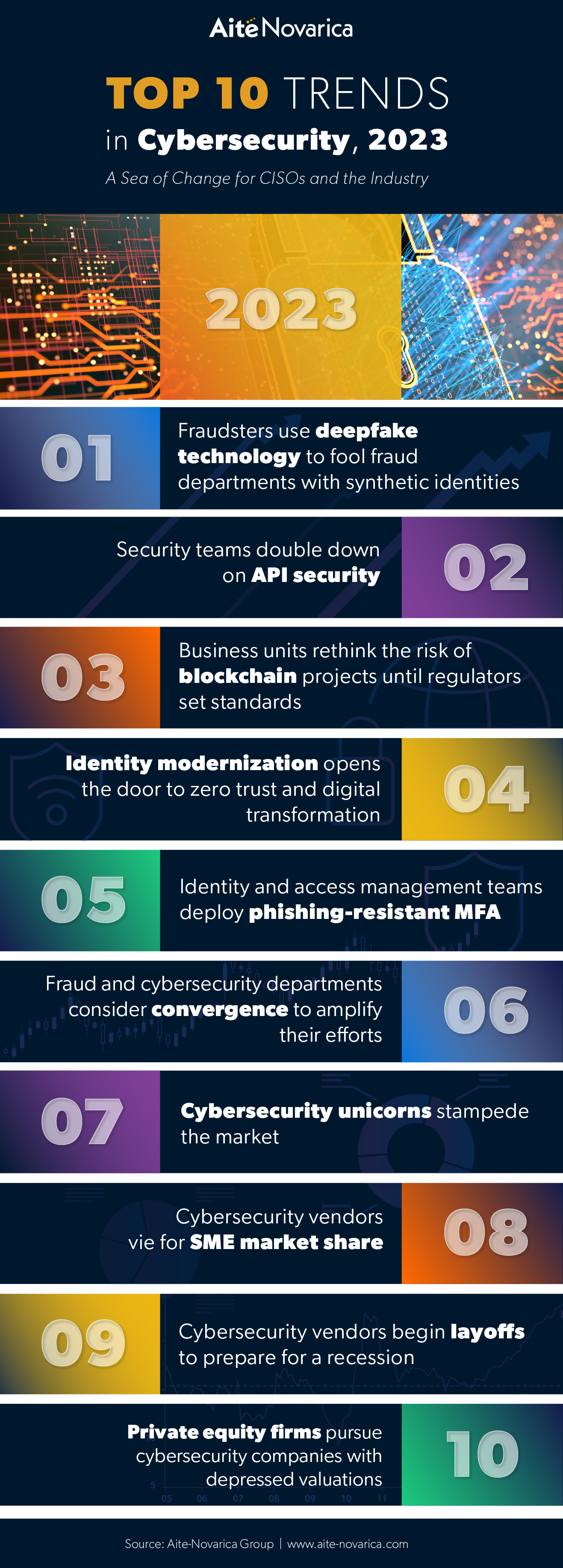



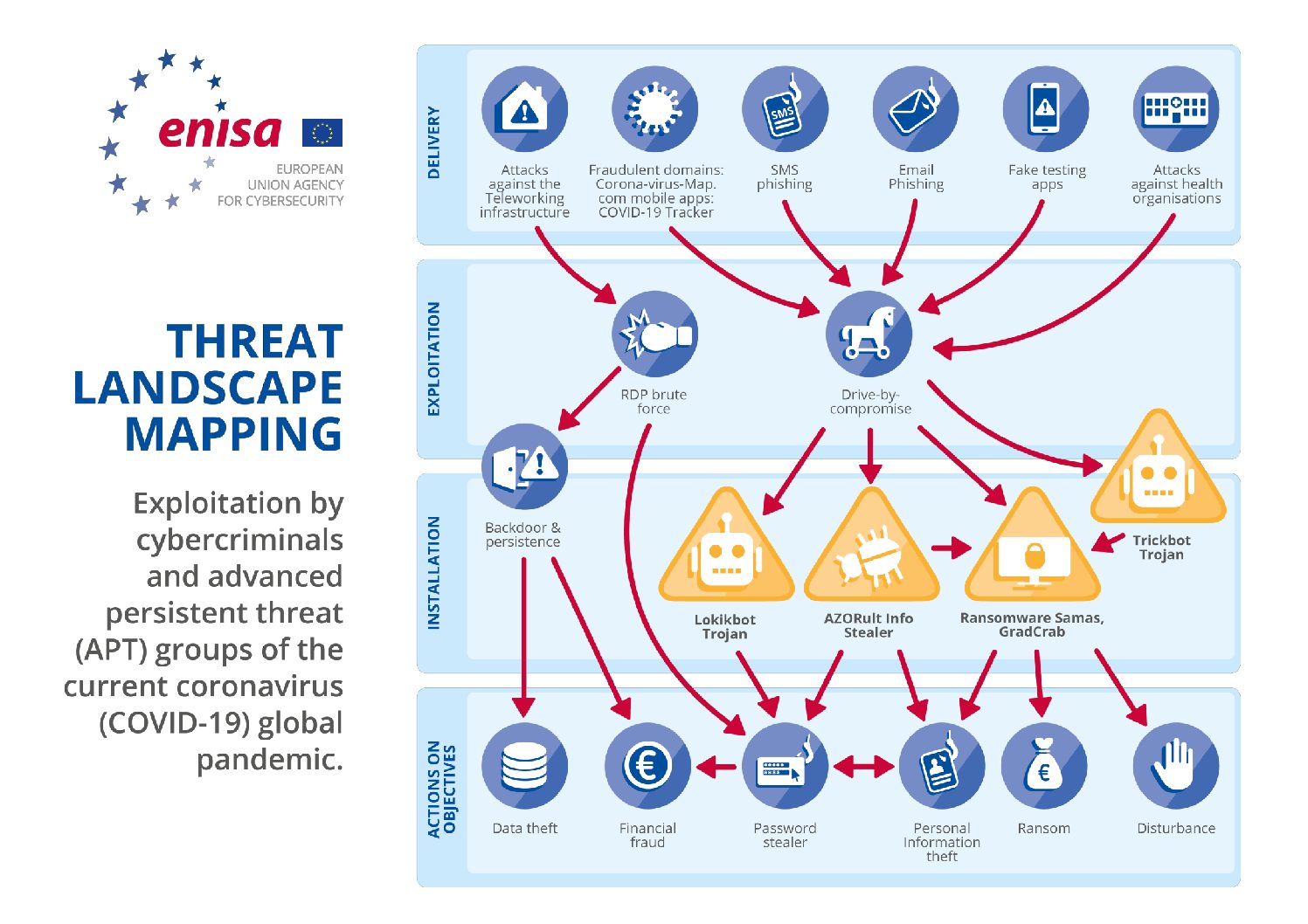
Closure
Thus, we hope this article has provided valuable insights into Cybersecurity Trends 2025: Navigating the Evolving Threat Landscape. We thank you for taking the time to read this article. See you in our next article!